- How CNAM Works ?
- CNAM Features
- CNAM Architecture
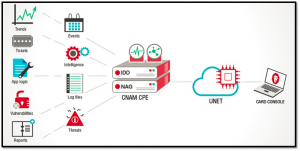
- CNAM – the system and its components
- Plans & Comparison
Comprehensive Netowrk Attack Monitoring (CNAM) is a complex engine that simplifies threat management. It builds threat models from around the globe and delivers quality decision making to customers.
CNAM uses five primary function modules at the core of the threat detection engine, these modules are tuned by experts for each deployment scenario. Here is a breakdown and brief function of each module.
- Traffic anomaly engine - detects DDoS, BotComs, proxies and p2p violations
- Managed intrusion detection - detects custom attacks on systems and applications
- Malware detection engine - detects worms, malware and APT
- Threat intelligence - shortens the detection time using external threat awareness
- Event correlation - qualifies attackers across locations and provides measurability
CNAM helps you improve the visibility of your network and detect threats accurately in the smallest time window. The primary function modules have direct integration with application libraries.
How does CNAM integrate ?
A good threat management system is required to be flexible, it should be able to integrate and operate seamlessly with existing infrastructure. CNAM offers simplicity in design to its customers.
CNAM delivers a comprehensive set of unique features that streamlines and automates your threat detection capabilities. Real-time results from CNAM deliver the missing threat visibility in enterprise networks.
A Comprehensive Threat Management Platform

CNAM brings all the right components required to operate an effective security program but without the expensive overheads
- Entire threat detection stack in the managed framework, available in SaaS model with no upfront investment
- Learns your environment and can be customized to meet your needs
- Visibility at all layers to detect the most sophisticated attacks before they happen
Cutting-Edge Packet Analytics

CNAM delivers next generation threat detection using packet level profiling and analytics capabilities.
- Auto’magically’ identify ratio deviations in packet trends to call-in correlation modules
- Detect changes in your environment using a profile based anomaly engine identifying every new destination, domain, URL, filename, or user.
Triggered Threat Correlation Engine

CNAM’s engine is built ground up to correlate around the attack. CNAM’s triggers can concurrently process several hundred correlation module
- Reduced implementation time required for tuning and environmental learning due to attack centric correlation
- Expand correlation and graph logic without worrying about the number of active rules
- Respond to threats in real-time, as modules are triggered at the time of the event and not on a set time window.
Real-time Data Science And Continuous Integration Engine

CNAM’s continuous integration engine profiles threats, packets and data usage to identify attack indicators. CNAM is designed to work autonomously on customer policies to maintain accuracy and real-time capabilities.
- Managed detection and correlation systems give customers the freedom to operate without in-house expertise
- Threat intelligence is continuously shared and integrated in real-time
Distributed Core Control plane And A Meshed Data Transport Framework

CNAM’s distributed control plane architecture is used for instant deployment and management of remote systems and policies.
- Enforce standardized security rules across your vast enterprise network
- Instantly scalable to new devices added with easily configurable node-specific correlation and detection
Integration+

Advanced Threat Detection, Attack Correlation and Enabled Response are delivered as a single solution with CNAM. Plus further integration with your business application gives you complete information security coverage.
- Threat management that encompasses the complete enterprise architecture
- No backdoors or vulnerabilities open to exploitation
Deployment

We drive the entire deployment process efficiently while you can safely concentrate on your business. CNAM's deployment is quick, easy and trouble-free enabling it to be up and running in no time.
- Deploy quickly and easily on commodity hardware without the hassles of large scale project management and expensive consultants.
- Our Big Data back-end enables a flexible and seamless threat management solution that can evolves as you do.
- Dedicated deployment resources to provide support whenever needed
Log Management

Instead of giving you bulky log reports of all events, CNAM gives you summarized logs after performing aggregation, storage, indexing and searching of large amounts of system data.
- Easy to read log reports
- Conveniently shared for audit and security requirements
Compliance

With CNAM, you don’t need any additional compliance tools. CNAM satisfies your compliance requirements by generating logs and reports as per your needs.
- On boot compliance with regulatory requirements
Data Residency

All transactional and attack data remains on the customer's network with only summarized result-sets leaving the network for correlation
- Comply with stringent data privacy and data security regulations
- Confidential business critical information stays within your network
Ease of deployment is one of the primary design goals of the service. CNAM deployments are easy to design and offer several customization options. CNAM provides some key benefits for system architects.
- CNAM is able to deploy in a variety of network types and conditions
- It is able to offer virtualized deployments for smaller requirements
- For medium and small enterprises, CNAM components can be consolidated
- Clustering features allow CNAM to scale seamlessly
- CNAM offers scalability at all levels with a single threat management window
A large number of complex deployments are delayed or fail due to the inability of a system to adapt to the environment. CNAM is different, it is able to comply with the demands of the architecture and still deliver value to its customers. CNAM provides highly effective detection profiles for attacks from the internal and the external networks. CNAM allows a large amount of customization in attack detection modules across deployment architectures.
CNAM brings extreme flexibility and scalability into your security infrastructure. With its distinguished component blocks, CNAM can be deployed effortlessly into your organization.
Benefits of CNAM
SIEM tool powered by Netmonastery and SOC support provided by Simba Technology – Customer does not have to go to 2 different vendors
** SOC : Security Operations Center
Hardware, Software, Hosting and People – All included in one package
False positives are reduced by mapping threats with asset vulnerabilities through a VA module
Competing solutions provide analysis of the event with a delay
Simba technology as a service provider has access to multiple client’s security architecture
Logs are maintained within the customer network
CNAM uses cutting-edge algorithms and the power of the cloud to actively detect and respond to attacks on your critical IT infrastructure. It implements advanced correlation rules and detection mechanism coupled with a global intelligence network to deliver top notch security presented in an intuitive dashboard.
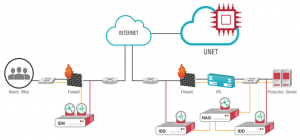
The Umbrella Network (UNET)

The UNET is a global facility used by CNAM to deliver real-time threat intelligence to its customers. The UNET aggregates intelligence from two networks viz. the CNAM customer network and the partner network. UNET is a network of global presence points called as Point-of-Presence (POP).
- Each POP has a correlation management and intelligence processing facility
- All POPs are directly controlled by the CNAM team at NETMONASTERY
- Customization on each customer is performed centrally from the CNAM Threat Center
Intrusion Detection Device (IDD)

The IDD is the primary whistle blower for the CNAM service, it uses multiple technologies for detecting attacks in real-time. Each IDD is customized to the needs of the network and is monitored using unique correlation rules deployed by the CNAM Threat Center. Detection modules in the IDD are updated continuously to keep up with the changing threat landscape.
- The IDD contains industry standard and proprietary technology that detect attacks
- It houses a traffic anomaly engine for floods
- It also includes a collaborative worm detection engine to detect outbreaks
Network Aggregator (NAG)

NAG is a local event collection and analysis engine, that is responsible for executing the correlation logic on the accumulated data. The NAG ensures that all the data collected by CNAM remains within the network perimeter. The NAG is in constant connectivity with the UNET which supplies real-time threat intelligence for accurate decision making.
- The NAG collects event logs from various sources and locally processes them
- This device pulls up correlation strategies from the UNET
- The NAG applies the correlation strategies on the current event thread to develop local intelligence and a trend
SIMBA CNAM Plans
|
|
|
|
|---|---|---|
| Real-time threat intelligence | Includes CNAM Plus features | Includes CNAM Pro features |
| Attack detection system | Server / device log integration | Application integration |
| Multi-layer correlation | Dedicated reporting console | Detection signature customization |
| Dashboard and reporting | Custom correlation rules | Custom correlation modules |
| Profile management | Collaborative outbreak detection | Application integration support |
| 24x7 Support-ops | Event monitoring and archiving | Local decoy strategy |
| Dedicated account manager | Threat strategy consulting | |
| Instant threat notifications | API Integration | |
| Get Quotes | Get Quotes | Get Quotes |
SIMBA CNAM Comparison
|
|
|
||
|---|---|---|---|
| INTRUSION DETECTION | |||
| Dedicated intrusion detection | |||
| Continuous signature updates | |||
| Traffic anomaly engine | |||
| Collaborative outbreak detection | |||
| Customised signatures | |||
| THREAT CORRELATION | |||
| Dedicated correlation engine | |||
| Multi-devide correlation | |||
| Real-time event processing | |||
| Customised correlation rules | |||
| Customised correlation modules | |||
| COLLABORATIVE INTELLIGENCE | |||
| 3rd Party intelligence | |||
| NM Honeynet intelligence | |||
| UNET intelligence | |||
| Global threat intelligence | |||
| ANALYSIS AND REPORTING | |||
| CARD(web based) analysis console | |||
| Threat management system | |||
| Periodic reports | |||
| Real-time incidents reports | |||
| Dedicated reporting console | |||
| Instant threat notifications | |||
| APPLICATION INTEGRATION | |||
| Periodic exposure evaluations | |||
| Application security analysis | |||
| Advisories on application security | |||
| Application security integration lifecycle | |||





